July 05, 2012
By Jayendra Pathek, Randy Abrams
NSS Labs has recently encountered a phishing campaign targeting American Express customers. The phishing emails ask users if they have recently reset their password, or verified their user ID for their American Express Card account online. Where some phishing attacks simply attempt to obtain a user’s account number and PIN when they click on a link, this attack is much more sinister.
The campaign NSS Labs has researched is directing users to a website that uses the popular Blackhole exploit kit. When the user arrives at the landing page, and even before they can ascertain whether or not they might be at a legitimate website, the exploit kit has already profiled their computer and determined if there are vulnerable applications to exploit. If there are vulnerable applications, as is more often than not the case, a Trojan downloader will be installed. At this point, even if the user has determined that something is amiss it is too late, as Blackhole has already completed its work and the installation of malicious software is proceeding independently in the background.
In NSS Labs’ testing, our analysts visited the exploit kit landing page using a PC that had vulnerable versions of Adobe Reader (ver: 8.1.1) and Java (ver: Jre6U27.) As a result, we were served with Adobe and Java exploits, leading to the installation of a Trojan downloader with the MD5: bcb391c5edd24abb419528b87896cd91 installed in the directory C:\Users\\AppData\Roaming\Feezl\. The Trojan downloader then proceeded stealthily to download and install a variety of other malicious files from the Internet.
The detection ratio for this Trojan on VirusTotal is extremely poor. Only 6 out of 42 antivirus (AV) products detected the file when we last checked.
The names reported by the six AV products already provide some insights even before we begin a more detailed analysis:
TR/Crypt.XPACK.Gen (AntiVir)
W32/Kryptik.WDV!tr (Fortinet)
PWS-Zbot.gen.xs (McAfee)
PWS-Zbot.gen.xs (McAfee Gateway Edition)
Bck/Qbot.AO (Panda)
Mal/EncPk-MP (Sophos)
Both Zbot and Qbot are backdoor Trojans that are used to download a variety of other malicious files. In this case the PWS in front of Zbot is how McAfee informs us that this is a password stealer. Crypt, Kryptik, and EcnPk are advising that there is packing/encryption used to evade detection and analysis.
The Blackhole exploit kit is known to be rented and/or sold for use by a variety of criminals and criminal organizations. The exact attacks following the exploitation of a user will depend upon the motives and decisions of the specific attacker. In this case a variant of the Zbot.
The Exploit kit was hosted on 174.140.171.101 with ASN: AS46816.
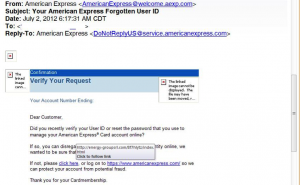
Fig 1: Email with Malicious link.
The diagram below walks the reader through the process to which the victim’s computer is subjected:
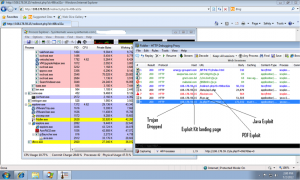
Fig 2: Infection Process
Once the Trojan download has been installed, anything from fake security products to keystroke loggers to eavesdropping software can follow. One particularly insidious attack of which corporations need to be aware is the installation of “ransomware”. Rather than attempt to exfiltrate, or remove, data, ransomware will make it inaccessible to the owner of the data until a ransom is paid. This means that once the ransomware is activated, there is not necessarily any network traffic that might trigger IDS/IPS solutions or firewalls; data is encrypted locally and the unencrypted files are wiped. Any data that has not been backed up is likely to be lost, and attempts to pay the “ransom” usually only result in credit card theft.
Files Downloaded by the Trojan in this Specific Attack
1. File Name:0_0u_l.exe
2. File Name:34396531.exe
3. File Name:xioceq.exe
A preliminary review of the VirusTotal results tends to indicate that the first file is a password stealer and that it is not very well detected. The second file maintains a backdoor to the system and also is not widely detected. The third file is a password stealer and backdoor, but is detected by 15 out of 43 products used. The probable reason for multiple password stealers and backdoors is that a broker is being paid by multiple criminals to install malware on systems for a variety of purposes.
The critical take-away for both enterprise and home users is that the Blackhole exploit kit has an easily attackable Achilles heel: patching! Fully patched machines are not vulnerable to Blackhole. With a patched machine, even those users who follow the link in the phishing email would come away unscathed (providing they enter no confidential information on the fake webpage, of course!) regardless of whether they use OS X, Windows, or Linux. Users with outdated versions of Adobe and Oracle products, however, don’t stand a chance.
Original Article


