Are recent Sophos blog post explains how some recent ransomware makes it ESSENTIAL to have good backups of your data…
Ransomware is malicious software that attempts to extort money out of unsuspecting users, normally by locking them out of their machines. This isn’t the first time (or even the second) that we’ve seen such malware in the last few months, but lately there has been a trend of a more sinister type of ransomware.
Instead of simply employing tricks to lock you out of your computer, crypto-ransomware holds your files (documents, photos, music, movies, etc.) hostage by encrypting them. This makes remediation a lot more difficult than just removing the malicious infection, as your files also need to be decrypted.
Last week, SophosLabs saw new ransomware samples employing this technique. On infection, the malware searches for specific types of files (using a list of over 110 file extensions; .doc, .jpg, .pdf, etc), encrypts them, and renames the now unreadable file with a .BLOCKAGE extension. The following ransom message is then displayed to the user:
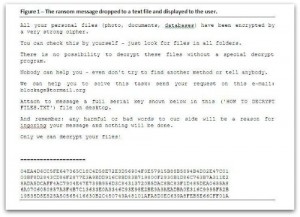
All your personal files (photo, documents, databases) have been encrypted by a very strong cipher.
You can check this by yourself - just look for files in all folders.
There is no possibility to decrypt these files without a special decrypt program.
Nobody can help you - even don't try to find another method or tell anybody.
We can help you to solve this task: send your request on this e-mail: [email protected]
Attach to message a full serial key shown below in this ('HOW TO DECRYPT FILES.TXT') file on desktop.
And remember: any harmful or bad words to our side will be a reason for ingoring your message and nothing will be done.
Only we can decrypt your files!
As all your files are being encrypted, the malware also calls home and transmits a copy of the serial key to one of their command-and-control servers.
The scary part here is that they aren’t lying when they say that only they can decrypt your files. In fact, the malware makes use of some nifty public-key cryptography which is the same “one-way” (asymmetric) encryption that lets you safely shop online and access online banking.
The ransomware / malware generates a unique encryption key randomly every time it infects a computer, which it uses to encrypt your files (using the AES-256 “military grade” cipher algorithm). It then encrypts this using their public key.
The result of this becomes the unique serial key which is displayed to the user.
Unfortunately this means that only someone with their private key can decrypt the serial to get the key used to encrypt your files. To try and recover the private key required from just the public key alone (RSA 1024 bit) would most likely take millions of pounds of computation hardware and time and still probably wouldn’t be finished by the time I graduate from University (2 years’ time).
While the cryptography being used here to hold your family holiday photos/retro music collection/letters from your girlfriend to ransom is very sophisticated, further analysis of the ransomware / malware itself reveals it to be not so smart. In fact, I would go as far to say the samples that I have seen are the work of an amateur malware author.
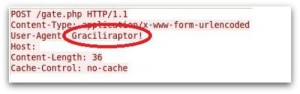
The majority of the ransomware / malware code is not packed or protected in any form like I have come to expect from any sophisticated malware. Additionally, there are several very unique strings present that serve no real purpose – in particular the string “Graciliraptor!” seen in packet captures from some samples.
Perhaps this is the author’s online persona, or a graffiti-esque ‘tag’ taken from the name given to a genus of theropod dinosaur from the early Cretaceous Period, meaning “graceful thief”. Either way, it makes detection of these malware samples a lot easier!
So the really worrying part here is that if this is indeed the work of a malware author wannabe, they have been able take advantage of some very clever crypto to wreak havoc on your system.
They do not even need to code these algorithms themselves; they can just use the crypto libraries (Microsoft Cryptographic API or equivalent) already present on your computer!
Paying the ransom is not recommended, and doesn’t even guarantee you will get your files decrypted. To me, this only emphasises the importance of having up-to-date anti-virus, and regular backups of important documents – just in case.
Original Article.
By Julian Bhardwaj
Our Take: Home users should get an affordable backup solution – we recommend Mozy for home users – it might take you a while to restore your data, but a while is better than having them locked up by some cyber-criminal… Here is a link for a FREE backup account of 2Gb – use it like a trial and upgrade to unlimited space if you like the service:
Mozy free account
Business users should get a BUSINESS GRADE BACKUP. If you are involved in financial services, or medical fields, you need to get a backup solution that addresses the regulatory concerns that your industry has.
Most importantly, ensure that data is ENCRYPTED. Having your own encrypted data uploaded to the cloud will ensure that if your get a destructive piece of ransomware, you can bring back your data when you get rid of it. We use and recommend our own backup solution – it’s so good, we’ll let you try it also – contact us for details!



